The 90-Day Cyber Culture Roadmap: A CISO's Plan to Build Human Risk Ownership
Move beyond basic awareness. Discover the 90-day roadmap to build a mature cyber culture and prove human risk ownership to your Board under NIS2.
.jpg)
Cybersecurity culture is the strategic transition from passive compliance to active defense, serving as the only effective barrier against the human element of cyber threats. In the era of the NIS2 Directive, relying on a simple "security awareness" completion log is no longer sufficient; regulators and boards now demand tangible evidence of human risk ownership across all levels of the organization.
For years, companies have relied on annual training sessions to "check the box." Yet, industry reports consistently show that the human element is involved in the vast majority of data breaches. This proves that passive knowledge does not equate to secure behavior.
The liability landscape has shifted for leadership. New regulations hold the C-suite personally liable for proving due diligence in cybersecurity governance. You cannot defend your organization—or your position—with a spreadsheet of course attendees. You need a mature culture where security is a shared value. This 90-day plan is your tactical roadmap to move your workforce from simple awareness to genuine human risk ownership.
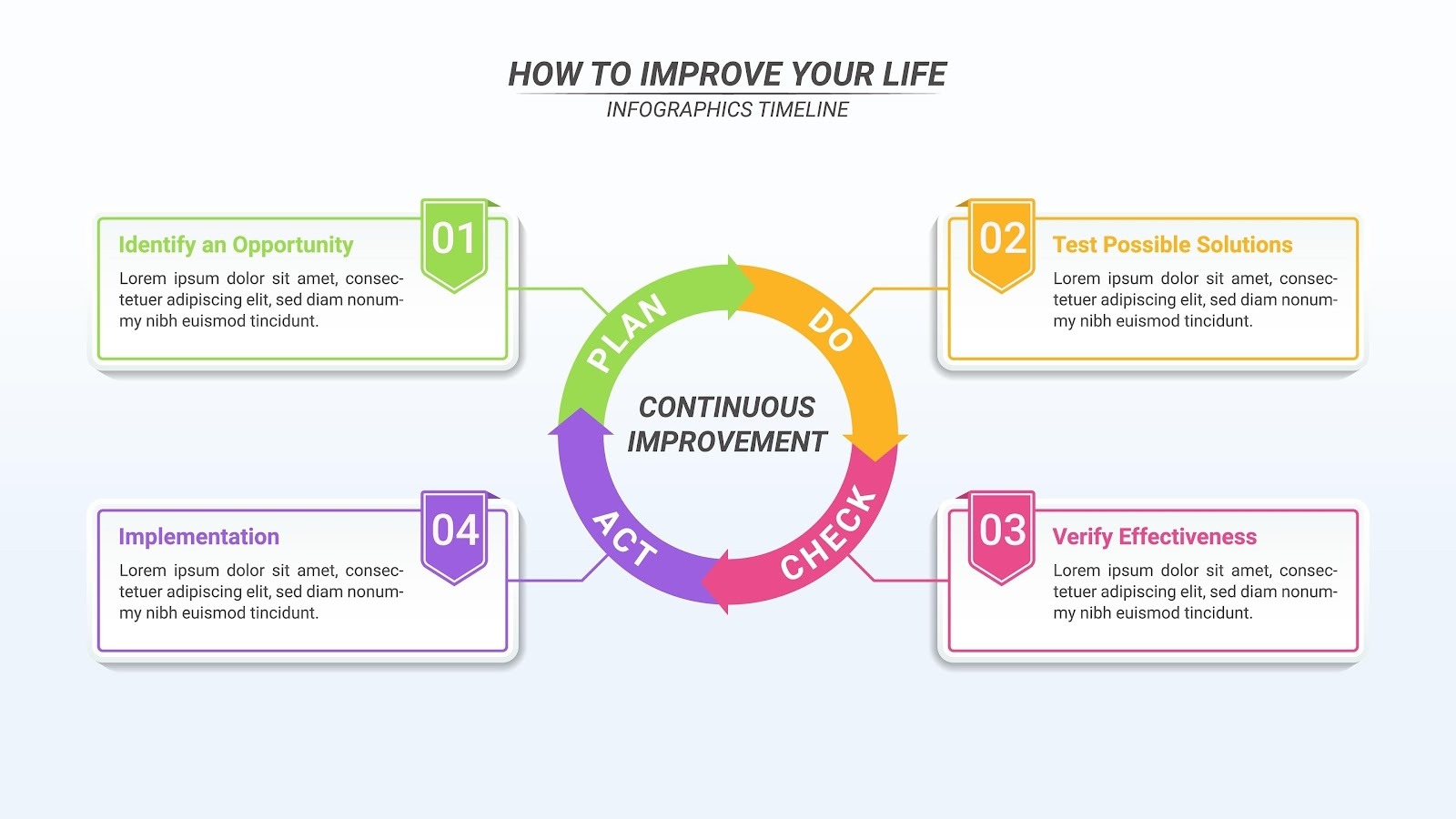
Before Day 1: Define Your Goal - What is Human Risk Ownership?
Human risk ownership is the strategic framework where cybersecurity accountability is decentralized, moving from the CISO's sole burden to a shared responsibility across every department. This shift transforms employees from passive targets into active defenders, ensuring that security decisions are made at the source of the risk—the human layer—rather than in the IT department.
From CISO Accountability to Distributed Ownership
Traditionally, security was dismissed as "IT's problem." However, under the strict liability standards of NIS2, that model is obsolete. You need a cybersecurity culture where specific business units own the risks they generate.
Leading analysts emphasize that we are currently witnessing a critical transition from simple Security Awareness & Training (SA&T) to Human Risk Management. This evolution proves that compliance is not culture. To achieve true resilience, you must move beyond counting course completions and start measuring behavioral change.
Defining Human Risk Ownership: It is the operational state where every team member understands their specific role in the security chain and is empowered to make risk-aware decisions without constant supervision.
The CISO + HR Partnership: Your Culture Leadership Team
You cannot build a resilient cyber culture from the SOC alone. While the CISO provides the "what" (technical risk data and threat intelligence), Human Resources provides the "how" (people-centric strategy and behavioral modification).
This alliance is the strategic driver of your 90-day human risk ownership plan. HR is crucial for identifying underlying friction points, such as tackling issues like burnout as a risk factor, which directly correlates with increased error rates and policy violations. When CISO and HR align, security becomes integrated into the employee lifecycle—from onboarding to exit—rather than being treated as an intrusive afterthought.
Phase 1 (Days 1-30): Secure Leadership and Establish Your Baseline
Phase 1 of your 90-day human risk ownership roadmap is about translation and diagnostics: translating technical risk into business liability for the C-suite, and diagnosing the true state of your cyber culture. You cannot manage what you do not measure, so these first 30 days are dedicated to securing budget approval and capturing a baseline risk score that serves as the indisputable "Before" picture for your future ROSI.
Day 1-10: Secure Executive Endorsement (with Data, Not Fear)
The most common mistake CISOs make is approaching the board with FUD (Fear, Uncertainty, and Doubt). In the context of NIS2, FUD is unnecessary; the law provides enough leverage. Your goal is to present a business case that frames human risk ownership as a liability shield.
Executives need to understand that under current European regulations, they are personally liable for gross negligence in cybersecurity governance. Do not ask for budget for "training"; ask for resources to build a defensible due diligence trail. Present the problem in financial terms: "NIS2 mandates this level of oversight, it reduces our potential breach cost, and here is the 90-day plan to show measurable ROSI."
Day 11-20: Establish Your Baseline Human Risk Score
Once you have the green light, you need data. You cannot demonstrate improvement in Month 3 if you don't know where you stood in Month 1. During this period, run a diagnostic phishing simulation and a culture survey.
Crucially, this must be a "blind" test. The goal is not to catch people or punish them, but to observe natural behavior. Industry statistics suggest that unmanaged organizations often see click rates above 20%. However, click rate is a shallow metric. You need to establish a holistic baseline risk score that aggregates three distinct behaviors:
- Vulnerability: Who clicked?
- Defensibility: Who reported the threat via the official button?
- Recurrence: Who is a repeat offender?
Day 21-30: Segment Your Audience and Define Your "Win" (KPIs)
A "one-size-fits-all" approach is the fastest way to kill cybersecurity culture. A Finance Director faces different threats (BEC, invoice fraud) than a Developer (credential theft, supply chain). Use the data from your diagnostic to segment your user base into groups such as High-Risk Departments, New Hires, and the C-Suite itself.
Finally, before moving to Phase 2, you must set the rules for success. Define clear KPIs for your 90-day sprint. Avoid vague goals like "better awareness." Instead, set concrete targets such as "Increase Phishing Report Rate by 20%" or "Reduce Repeat-Clicker Rate by 50%." These are the metrics that will prove the value of your program to the board.
Phase 2 (Days 31-60): Engage, Gamify, and Build New Cybersecurity Culture Habits
Phase 2 focuses on transforming passive knowledge into active human risk ownership and a proactive cybersecurity culture through behavioral conditioning. It is not enough to simply inform employees of risks; you must simulate them in a safe environment to instill reflexive defense habits. By combining realistic attack simulations with positive reinforcement, you move from a culture of compliance to a cybersecurity culture of instinctive defense.
Day 31-45: Launch Your First High-Engagement Campaign
Static, text-based phishing templates are not enough. To prepare your workforce and strengthen human risk ownership against today's threat landscape, you must launch a multi-vector campaign that mirrors the sophistication of actual attackers. This means moving beyond email to include context-aware vectors like a vishing or QRishing simulation.
If you only test for email clicks, you are leaving the "side doors" wide open. For high-risk segments (such as Finance or C-Suite assistants), a well-timed QR code scam (QRishing) disguised as a parking validation or multi-factor authentication request is far more effective at revealing vulnerabilities than a generic "password reset" email.
Day 46-55: Introduce Gamification That Drives Behavior
Gamification is often misunderstood as "badges for children." In reality, it is a scientifically backed method to trigger the dopamine release required for habit formation. According to the Fogg Behavior Model, behavior happens when Motivation, Ability, and a Prompt converge. Gamification increases motivation.
Shift the focus from "shaming failures" to "rewarding detections."
- Build "Defender" Leaderboards: Rank departments based on who reports threats the fastest, not just who clicks the least.
- Create Bounties: Offer tangible rewards (gift cards, extra time off) for employees who spot and report a real threat that slipped past the SEG (Secure Email Gateway).
Example Campaign: "The Deepfake CFO"
- The Setup: Select senior managers receive a vishing call from an AI-cloned voice of the CFO requesting an urgent transfer.
- The Trigger: The call is preceded by a WhatsApp message (smishing) adding context.
- The Win: Employees who verify the request via a secondary channel (out-of-band verification) rather than acting immediately receive a "Cyber Guardian" recognition.
Day 56-60: Calibrate Your Training for Modern Threats
As you close Phase 2, your educational content must catch up to the simulations. Old-school advice like "check for spelling errors" is dangerous when attackers use LLMs to write perfect prose.
Update your micro-trainings to address the nuances of AI-phishing and deepfake voice scams. Furthermore, as Shadow AI becomes a massive regulatory blind spot, ensure you are clearly communicating the data handling rules for using tools like ChatGPT in the workplace.
Phase 3 (Days 61-90): Measure, Communicate, and Transfer Human Risk Ownership
Phase 3 is the strategic inflection point where your human risk ownership program transforms from a temporary initiative into a permanent operational standard. By Day 90, your goal is to shift from centralized IT monitoring to distributed human risk ownership, providing the C-suite with the concrete data needed to prove NIS2 due diligence and secure future budget.
Day 61-75: Measure What Matters (Resilience, Not Just Failure)
In the final month, run your second diagnostic simulation. The goal is to compare this data against the baseline you established in Day 20. However, do not fall into the trap of only looking at the "Click Rate."
A low click rate can simply mean employees are ignoring their email. The true metric of a healthy cyber culture is the "Report Rate." You want to see employees actively engaging with the "Report Phishing" button. This increase in your Report Rate is the primary indicator of organizational resilience. It proves that your workforce is not just passive, but acting as a collective sensor grid for the SOC.
Day 76-85: Create "Ownership Dashboards" for Managers
You cannot manage the risk of an entire organization alone. To achieve scale, you must decentralize accountability and enforce human risk ownership. This is the moment to introduce "Ownership Dashboards" to your department heads and VPs.
Stop sending them generic PDF reports. Give them access to dynamic data that shows their specific team's risk score, improvement trends, and participation rates. This transparency is the core of human risk ownership; makes risk visible and accountable, forcing managers to answer for their team's cyber hygiene just as they answer for their budget.
Visualizing the Dashboard: An effective Manager's Dashboard should display:
- Team Risk Score: A composite 0-10 score.
- Engagement Trend: Is the team getting better or worse?
- Top Risk Drivers: e.g., "High click rate in Marketing" or "Low reporting in Sales."
Day 86-90: Report Your 90-Day Strategic Outcomes to Leadership
Complete the governance cycle by returning to the Board with the results you promised in Phase 1 1. Present the delta—the measurable change in behavior between Day 1 and Day 90.
Do not just present a completion rate. Show the reduction in risk exposure and the increase in threat detection. This data report serves as your tangible proof of due diligence for NIS2 auditors, demonstrating that the organization has taken appropriate technical and organizational measures to manage risk.
Beyond 90 Days: From a Cyber Culture Sprint to a Continuous Program
Building a resilient cyber culture is a marathon, not a sprint. While this 90-day roadmap establishes the necessary baseline and leadership buy-in for NIS2 compliance, true human risk ownership requires a continuous, automated program that evolves alongside emerging threats. You cannot "fix" human behavior once and walk away; it requires consistent reinforcement.
The momentum you have built in the last three months must now be operationalized. If you stop now, the behavioral curve will regress within weeks. The next step is to integrate these sporadic wins into a structured annual training calendar. This ensures that your rhythm of simulation, education, and feedback persists without causing administrative burnout.
Automation is your ally here. You must continuously refine your user segmentation based on behavioral data and update your simulations to match the threat landscape. You have laid the auditable, data-driven foundation; now you must maintain the standard.
Frequently Asked Questions


Security awareness is simply "knowing" the rules (often measured by completion rates). Cybersecurity culture is "doing" the right thing instinctively; it is the collective mindset where human risk ownership protects the organization even when no one is watching.


Yes. NIS2 explicitly allows for temporary bans on executives from holding management positions if gross negligence is proven. Lack of effective training and oversight (specifically, a weak cybersecurity culture) can be cited as evidence of negligence during a breach investigation.


NIS2 requires a comprehensive approach to risk. Vishing (voice phishing), Smishing (SMS phishing) and QRishing (QR phishing) bypass traditional email security filters, representing a significant gap in many organizations' technical defenses that only a well-trained human firewall can close.


HR integrates security competencies into job descriptions, onboarding, and performance reviews. This ensures cyber resilience is treated as a core professional value and soft skill, facilitating true human risk ownership, rather than just a technical rule enforced by IT.


While CISOs often track "Report Rates," Boards care about "Risk Reduction." You must translate your metrics into financial terms, for example: "We reduced the probability of a successful ransomware entry by 40% based on our simulation data," rather than just showing participation percentages.


Focus on the Cost of Inaction. Compare the investment of the program against the potential fines of NIS2 (up to 1.4% or 2% of global turnover) and the operational downtime costs of a ransomware attack caused by human error.









